For business in change
Cybersecurity
Simplify security within the existing IT infrastructure and make it safer with Software Defined Security.
About our Services
Cybersecurity
Cyberattacks continue to grow in both number and complexity. For that reason, it is vital to think long and hard about a security strategy and not regard it as something incidental. With a Software Defined Security (SDS) approach, security in the IT environment is implemented, monitored and managed by software and immediately placed beneath the application layer in the IT infrastructure. This is far more efficient and safer than security that is only set up from a network or firewall perimeter. The scalability of the environment will increase and decrease its scope depending on the underlying infrastructure and necessary resources.
Optimum protection of business data
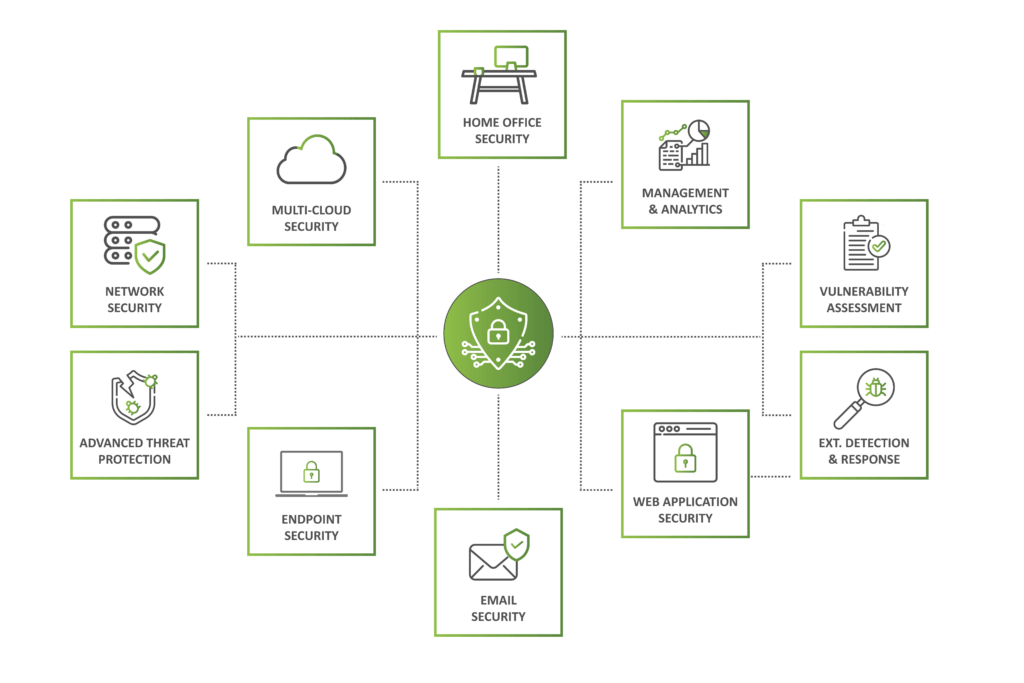
Various security solutions

Network security
Suspicious activity on your network is intercepted by Advanced Threat Detection Appliance. For this we make use of all of the following: IDS, Packet sniffers, Network Behaviour Analysers and Sandboxes, plus Detection and Response techniques.
Server security
Security for your data and services, whatever their form. This can be in the form of physical or virtual servers, on-premise, in the cloud or in containers.

Endpoint security
Ensure optimum protection for all devices whether they are fat or thin clients, POS systems or devices for other purposes.

Email security
Ensure the necessary protection for your mail platform, on-prem and in the cloud (O365), with the help of advanced spam detection, filtering and cleaning methods.

Mobile security
Mobile device management, mobile device security, data protection and application management all come under this.

Cloud
security
Ensure optimum security for all your data, services and applications as well as the associated infrastructure such as containers, servers and storage in the cloud.

Management and analytics
Through our managed services, we take control of all or part of your security environment. We monitor your security incidents and maintain your security platform.

Advanced threat protection
The combination of various security solutions in a single platform allows us to protect you against advanced attacks.

Vulnerability assessment
We use this assessment to gather information about which vulnerabilities hackers can use to penetrate your environment and how you can solve these weaknesses.

Extended detection and response
With XDR, you can perform forensic analyses, launch threat hunting and actively use IOCs in your environment.
Comprehensive end-to-end security framework
Benefits of software-driven security

Availability
Continuity of business operation, during and after unforeseen events.

Automation
Simplify management and clarify results.

Simplicity
Detections at all levels are correlated and combined into a single, intelligible whole.

Pricing
Transparent pricing per asset means you will not encounter unexpected costs.
Our most used technologies
Where can we support you
Our most used technologies
Where can we support you
Our reference cases
WHAT OUR CUSTOMERS SAY
O365 resides in the cloud and provides application recovery capabilities. However, securing this data remains the ultimate responsibility of companies. With its “Backup for Microsoft 365,” Veeam offers a full-fledged backup solution that also supports the Cherriis Web portal.. Setting up, managing and continuously optimizing this portal is done in close cooperation with Integri in the form of a SaaS solution.
BO Partner is a reseller of IT services with clients such as Bulo, Nathan, Eagle Stone and Nonet in its portfolio. Recently, they decided to focus more on their higher-end IT services and rely on a third-party Service Provider to manage their infrastructure.
O.L.V. van Lourdes Hospital Waregem is a general hospital that is part of the regional hospital network E17 and offers almost all services. They have 264 licensed beds and approximately 800 employees. With the slogan ‘together we guarantee the best possible care’ they are fully committed to providing their patients with excellent care, tailored to each individual’s needs and wishes. In order to fulfill and keep this promise, they invest in innovative projects to improve quality systems and optimize processes.
Get started on your digital transformation today
We would be happy to learn more about your business during a no-obligation meeting.